Using shell scripts to control, destroy, or get anything on a Linux server, hackers can gain tremendous value through some clever attack methods, but most attacks leave behind. Of course, these traces can also be hidden by methods such as shell scripts.
Finding evidence of the attack begins with the traces left by the attacker, such as the date the file was modified. Each file in each Linux file system holds a modification date. When the system administrator finds the file's recent modification time, it prompts them that the system is under attack and takes action to lock the system. Fortunately, however, the modification time is not an absolutely reliable record, and the modification time itself can be spoofed or modified. By writing a shell script, an attacker can automate the process of backing up and restoring modification time.

Most Linux systems include tools that allow us to quickly view and modify timestamps, the most influential of which is "Touch", which allows us to create new files, update files/filegroups for the last time "touched".

If the file does not exist, running the above command will create a new file named "file"; if it already exists, the command will update the modification date to the current system time. We can also use a wildcard, such as the string below.

This command will update the timestamp of each file in the folder it is running. After creating and modifying a file, there are several ways to view its details. The first one uses the "stat" command.
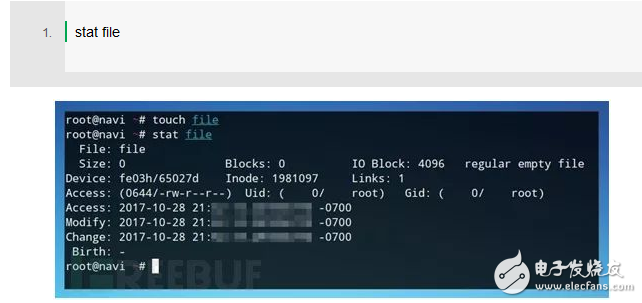
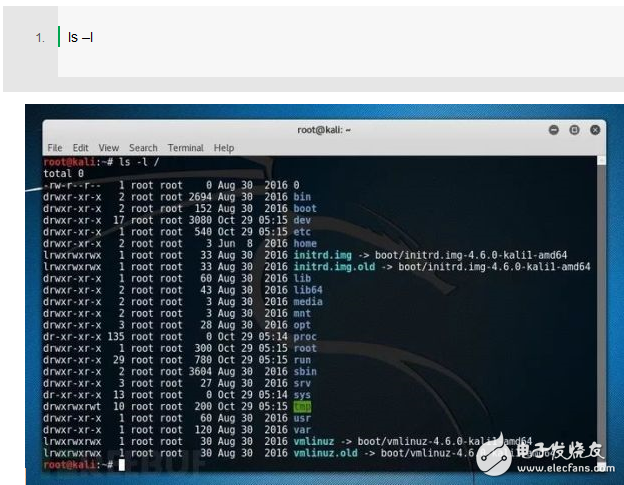
Running stat returns some information about the file, including access, modification, or update timestamps. For a batch of files, you can use the ls parameter to view the timestamp of each file. Using "-l" or "long", the command will list the file details, including the output timestamp.
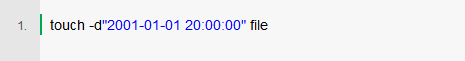
Now you can set the current timestamp and view the timestamp that has been set. You can also use touch to define a custom timestamp. Use the "d" flag to define the date in yyyy-mm-dd format, followed by the time. Hours, minutes and seconds are as follows:
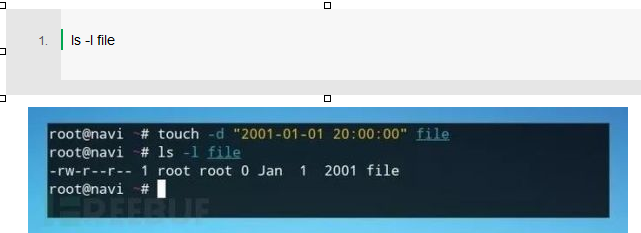
Confirm the modification information with the ls command:
This method is useful for modifying individual timestamps. This method is not very effective for hiding traces of operations on the server. You can use a shell script to automate the process.
Step two: Organize the shell scriptBefore you start writing a script, you need to think about what you need to do. In order to hide the trace on the server, the attacker needs to write the original timestamp of the folder to a file, and can return to the original file after we make any modification settings.
These two different functions are triggered based on the user's input or parameters, the script will perform the corresponding functions according to these parameters, and we need a way to handle the error. There are three possible actions that will be performed based on the user's input:
No parameters - return an error message;
Save timestamp tag - save the timestamp to a file;
Restore timestamp tag—Restores the timestamp of the file based on the savelist.
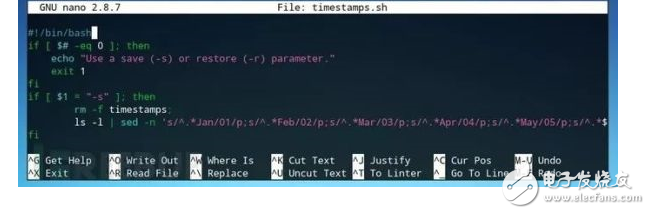
We can use nested statement if/or statements to create scripts, or assign each function to its own "if" statement based on criteria, optionally starting to write scripts in a text editor or nano.
Step 3: Start the scriptStart nano from the command line and create a script called "timestamps.sh" with the following command:
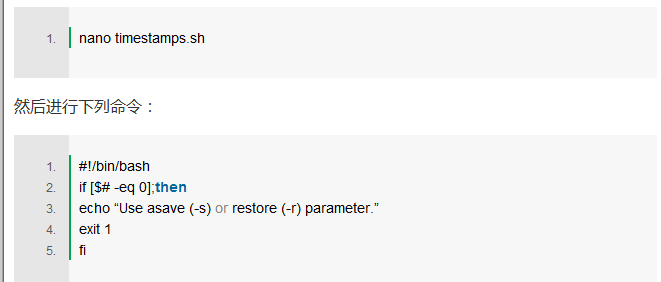
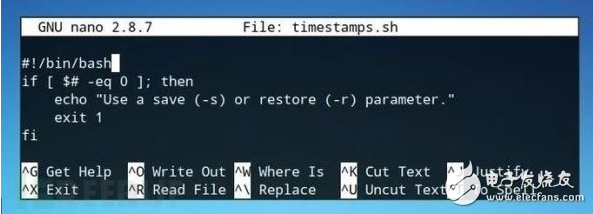
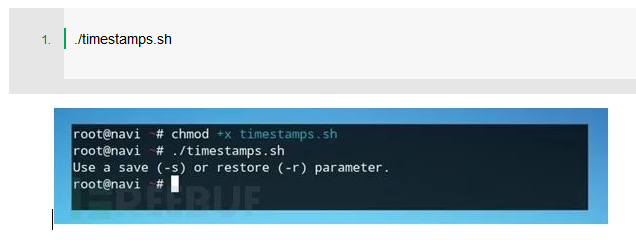
Press Ctrl + O in nano to save the file and mark it as a runnable script with the chmod command.

Then run the script to test the function of returning an error message when there is no parameter. If the script returns our echo statement, we can proceed to the next condition.
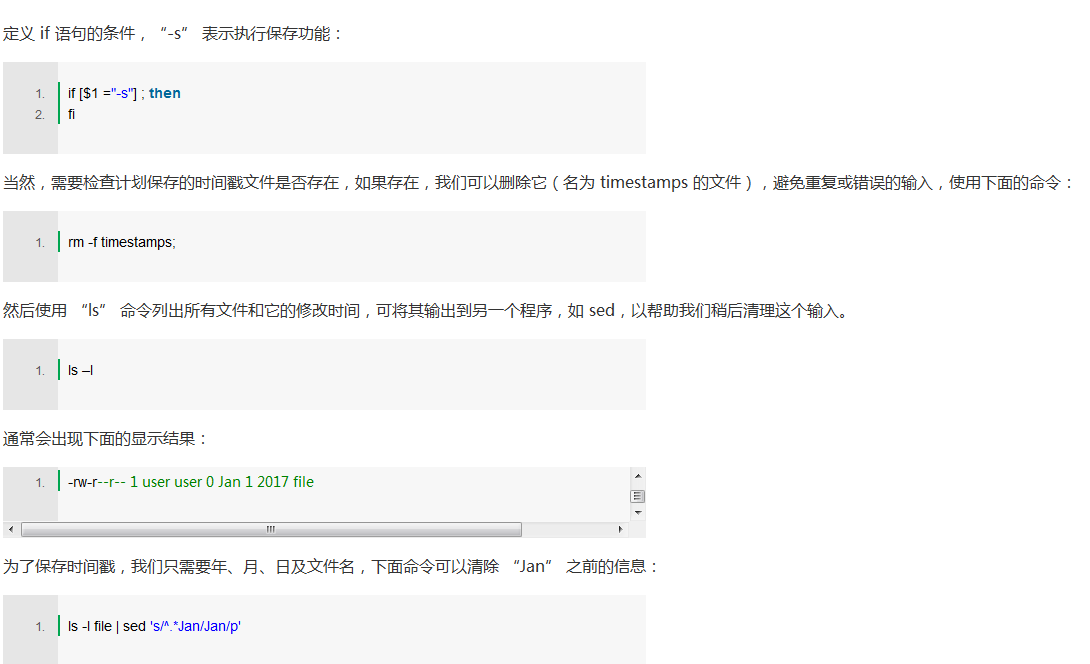
This shows the information we need for the program, just need to modify the month format to a number format:
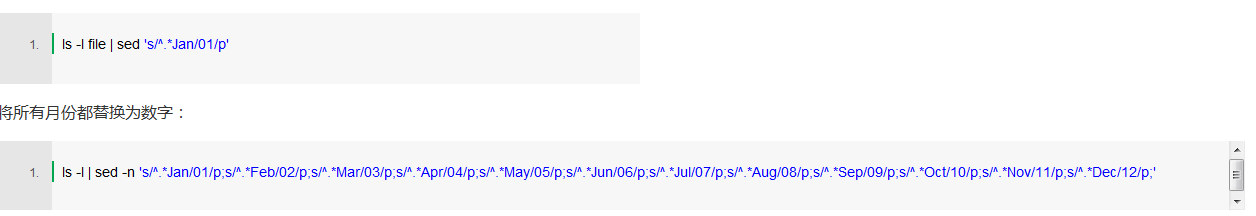
Running in a folder we will see the results shown below:
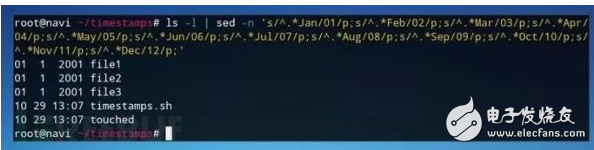
Then send the output to the file named "timestamps" via """:
Do echo $x | ls -l | sed -n 's/^.*Jan/01/p;s/^.*Feb/02/p;s/^.*Mar/03/p;s/^. *Apr/04/p;s/^.*May/05/p;s/^.*Jun/06/p;s/^.*Jul/07/p;s/^.*Aug/08/p ;s/^.*Sep/09/p;s/^.*Oct/10/p;s/^.*Nov/11/p;s/^.*Dec/12/p;' >> timestamps
At this point, the first two operations of the script are completed, and the results are as follows:
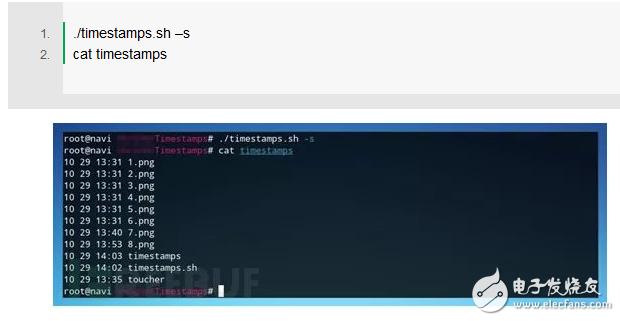
The test script can be marked with "-s" below, and the saved information can be checked with cat:
After saving the original timestamp, you need to restore the timestamp so that others are not aware that the file has been modified. Use the following command:
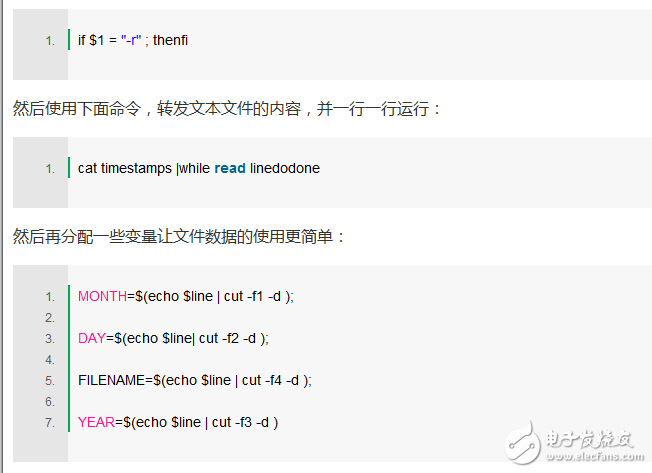
Although these four variables are consistent in the saved timestamp file, if the timestamp occurred in the past year, it will only display the time instead of the year. If we need to determine the current year, we can assign it as the year in which the script was written, or we can return the year from the system, and use the cal command to view the calendar.
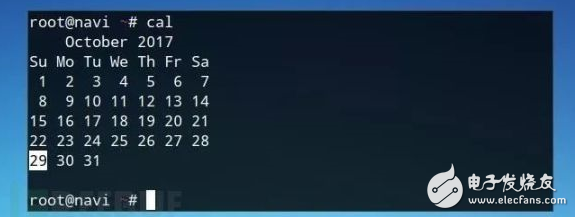
Then retrieve the first line and only display the year information you want:
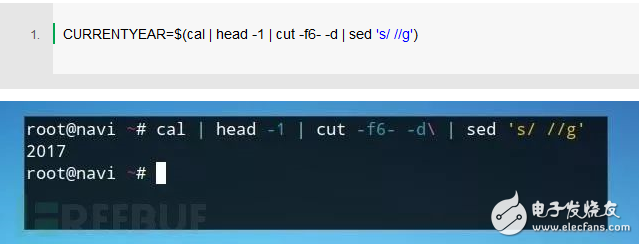
After defining all variables, you can use the "if else" statement to update the timestamp of the file based on the formatted date, using the touch syntax:
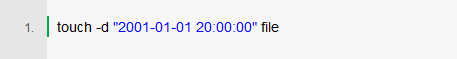
Since each time contains a colon, you can use the following "ifelse" statement to complete the operation, as shown in the following figure:
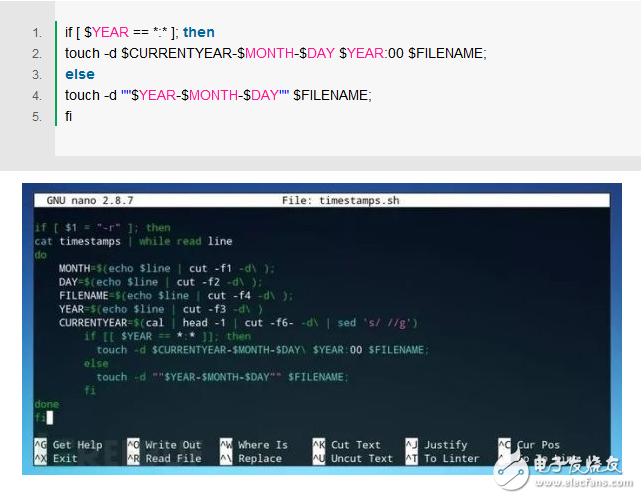
The commands used are mainly the following:
. /timestamps.sh –s save file timestamp
Touch -d "2050-10-12 10:00:00" * Modify all file timestamps in the directory
Ls –a confirm the modified file
. /timestamps.sh –r restores the original timestamp of the file
Finally, you can run "ls -a" again to check whether the timestamp of the file is consistent with the timestamp of the previous backup. The entire script is executed, as shown in the following figure:
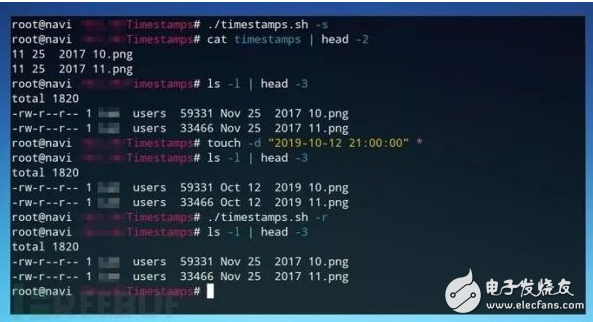
This script is only used to remove some traces left after attacking the server. In order to hide the traces, hackers must carefully consider each method used when implementing specific attacks against the server, and how to hide their traces after hacking the server.
Through the above introduction, we learned that timestamps are also "lie", so system administrators must be aware that many of their logs and protections can be manipulated, although it seems that there are no exceptions.
Modular Plug,modular jack rj45,modular jack cat6,mod plugs
NINGBO UONICORE ELECTRONICS CO., LTD , https://www.uonicore.com