It is generally believed that the home network does not have any targets worthy of hacking, but the Mirai bot attack in 2016 has greatly changed everyone's awareness of the wisdom of home.
In the case of Mirai, the virus continuously scans home Internet of Things devices, such as wireless routers or video cameras. The first generation of viruses only use the default account password of the networked device to try to log in, which can successfully infect millions of households. The device, and using these infected devices, successfully launched a large distributed blocking service attack (DDoS attack) on the telecommunication operator. In the past, DDoS attacks, usually hackers can only use thousands to tens of thousands of zombie servers to attack, as long as operators isolate IP one by one, they can be blocked smoothly; but Mirai can easily launch millions of devices and launch more than 1TB. Traffic attacks have caused many operators to do nothing.
In view of this, countries began to pay attention to the security of IoT equipment, from the UL2900 security standard derived from the US Cyber ​​Security National Action Plan proposed by former US President Barack Obama, to the top ten loopholes in OWASP's IoT security. The "Television Surveillance System Network Camera Network Security Standard" launched by the Taiwan Industrial Bureau and the fund policy conference brought together the industry's opinions was officially launched this year. On the other hand, security incidents such as network cameras being implanted in backdoors and home router poisoning are emerging one after another, and smart home security is gradually rising to national security issues. For example, in early 2017, D-Link and ASUS routers were accused by the US Federal Trade Commission (FTC). Although the settlement was reached later, the degree to which the US government attaches importance to the security of home security can be seen.
IoT devices will become the main target of hackers
Networked devices make threats ubiquitous, why do hackers start targeting IoT devices? The reasons are as follows:
1. The number of isomorphic devices is numerous and widespread all over the world. For example, once a brand camera is cracked, other camera intrusion methods are similar, which can quickly spread the virus.
2. IoT devices are always connected to the Internet, so they are easy to attack and are also a good target for springboarding.
3. IoT devices have few computing resources, so traditional antivirus or security software cannot be installed.
4. Most of the IoT devices do not have the function of automatically updating the software, and the vulnerabilities in the old software are easily penetrated.
5. Most IoT devices support cloud and App online, making it easier for hackers to reverse-decompose or cloud infiltrate from the App.
Readers may then ask why so many network security companies are unable to provide appropriate security protection. In fact, most of the current network security protection technologies are still based on very old signature scanning. The principle is to extract the captured virus sample behavior characteristics into a virus database, and then compare the incoming network traffic. And packets. For example, when it comes to entering and leaving the airport customs, the customs officers compare the photos of the wanted, and if they look like they are wanted, they will be stopped; but if they have not been registered on the wanted list, or if they have been shaped , you can pass the customs smoothly.
Signature scanning also encounters the same problem. With the current virus attack methods changing and spreading fast, antivirus companies often have no time to publish new virus features, or the virus characteristics are constantly deformed, and the virus samples have been swept around the world. That is, a zero-day attack. In addition, in order to save costs, the CPU and memory in the IoT device are mostly equipped with the minimum hardware specifications that are sufficient for the device to be used. It is difficult to accommodate a large security software embedding, let alone the space for storing a huge virus database. Although there are security vendors claiming to use the cloud virus database, the scan engine only needs to send the cloud comparison, but this method increases the delay of the traffic, and then increases the user's doubts about whether their privacy is also uploaded to the cloud. And still can't solve the problem of zero-day attack.
Smart home security advice
How do hackers break into these thousands of devices? Usually they will purchase some target devices to test for vulnerabilities. Most of these devices have weak protection mechanisms and open external network connections, such as routers or network cameras. Once the attack method is found, almost all types of devices with incomplete protection will be listed on the attack list. The hacker can develop a crawler program that can automatically scan such IoT devices, and then scan the network for leaks on the network. If you successfully invade your home router or camera, these programs will invade other devices through intranet scanning, which is hard to prevent.
For the self-protection of smart home users, the author suggests the following:
1. Try to use European and American brands or Taiwanese brands to export to the United States, and have been certified better. Usually, these manufacturers will not build backdoors, and when new security vulnerabilities appear, they will release updated software or firmware.
2. Changing the default password of all devices in the home becomes a strong password. It is safer to update the password regularly.
3. Update the software regularly.
4. Home-based laptops and mobile phones should try to install a closed operating system to avoid using open systems.
5. Be sure to turn off unnecessary cloud services and services that are remotely connected to the device through the App, because these services are likely to become a vulnerability for hackers.
6. Do not open and reply to unknown emails, especially to confirm the sender's email address. Since the sender's name can be spoofed, be sure to press the right mouse button on the sender field to confirm the sender's address. Go to a phishing email that is pretending to be sent by Microsoft or Apple and asking for a password confirmation.
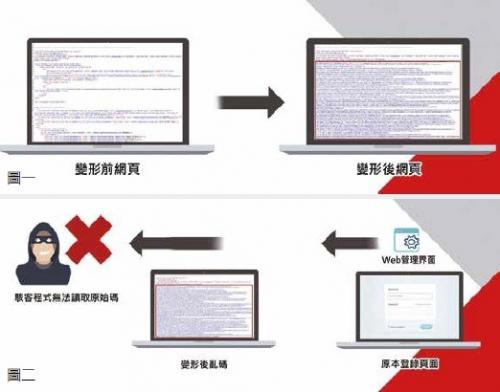
In addition to grasping the above points, many new network companies are now researching new IoT protection technologies. Take the Dynamic Transformation technology invented by the US startup Forceshield as an example. When a user browses a webpage protected by the Forceshield gateway software using a browser, the original page of the webpage is garbled and different each time ( As shown in Figure 1), when it is used in the management page of the IoT device, the hacker's virus program cannot read the source code of the web page (as shown in Figure 2), and can only give up the attack. This technology is not only thin and light (less than 2MB), it can be easily embedded in IoT devices, no need to update the signature code, the same technology can be used in App and cloud applications, can block most of the automated attacks of bots, has won many large websites and IoT device is used.
With the continuous increase of IoT devices, it is imperative to strengthen the security of the smart devices. It is expected that more and more startups will invest in IoT security protection in the future to meet the needs of users to use smart home devices with peace of mind.
Direct Current, or DC, electric motors power a wide range of applications. Biote Electric has helped clients source, design and develop small DC electric motors for a wide range of commercial applications. We have the knowledge and resources needed to help you find the best motor for your OEM application and budget.
Permanent-magnet DC motor can be directly
connected to a DC power supply, or an AC power supply operated through a
rectifier. You can control the speed of DC motor by adjusting voltage level.
Motor output is from 10W to 5000W and also can choose to equip with a Gear Box .
DC motors have simple appearance and easy to install so that our DC motors
provide a wide range of industrial applications.
Brushed Motors These are a more traditional type of motor and are typically
used in cost-sensitive applications, where control systems are relatively
simple, such as in consumer applications and more basic industrial equipment.

Brushed DC Motor
PMDC Gear Motor
Special PMDC Motor
Brushed Motor,Small Brushed Motor,Brushed Servo Motor,High Speed Brushed Motor
Ningbo Biote Mechanical Electrical Co.,Ltd , https://www.biotept.com