Cloud computing is a computing model that distributes storage and computing tasks on a resource pool composed of a large number of computers. This paper first introduces the three-tier structure model of cloud computing and multi-protocol label switching technology, and then proposes a multi-protocol-based protocol. The fourth layer structure of the label switching technology is used to ensure the reliability of data transmission in cloud computing. At the end, the function of this layer is described and the corresponding flowchart is given.
introduction
"Cloud" is like a huge resource pool, providing customers with many powerful and easy-to-use services. But when cloud computing brings many benefits, it also faces many challenges in cloud security. In this paper, a method for applying MPLS (MulTI Protocol Label Switching) technology to cloud computing to improve cloud security performance is proposed.
1 Cloud computing
There are currently many definitions of cloud computing, and there is no unified conclusion. The following definition is used in this article: Cloud computing is a business model that distributes computing tasks on a resource pool composed of a large number of computers, enabling users to obtain computing power, storage space, and information services on demand.
Cloud computing is usually based on the following three-tier structure, namely SaaS (Software asa Service. Software service), PaaS (Platform as Service, platform service), IaaS (Infrastructure asa Service, infrastructure service). SaaS provides a cloud service that users can enjoy through a browser. Users only need to pay according to usage, without installing any software or hardware. PaaS provides users with a series of platforms, such as SDK (Software Development Kit, software development tools), etc., users can easily program and deploy applications on it, and users do not need to worry about the operation and maintenance of servers, storage and network resources. IaaS provides users with computing or storage resources, so that users can load related applications, and the management of these resources is the responsibility of cloud providers.
2 MPLS technology
MPLS technology is a technology for fast data forwarding through label labeling. In the traditional method, routing analyzes the IP address of the packet header to determine the next hop and forward it. However, due to the long address, the forwarding speed is slow. In the MPLS network, once the data packet enters the LER (Lahel Edge Router, label edge routing), the label will be marked for the data packet, and then the next path of the data packet is determined according to the label, so that only the data packet label is read, and not read Taking the IP address of each data packet greatly improves the forwarding speed of the data packet. At the same time, the MPLS network will group packets with the same forwarding processing method into one category, called FEC (Forwarding Equivalance Claas, forwarding equivalence class). The same group of FEC will get the same processing in the MPLS cloud. At the same time, Frame Relay and QoS (Quality of Service) provided by ATM (Asynchronous Transfer Mode) switches classify the forwarded data packets to further improve network service quality and service diversification. Another advantage of MPLS is its protection of data privacy. In the MPLS network, the only visible route is the label carried on the data packet, without analyzing the load content of the data packet and the corresponding IP control information, and even encrypting the data if necessary .
3 Cloud architecture based on MPLS technology
The security mechanism of the IaaS layer describes the necessity of controlling the connection between the cloud and the client through interface technology, but it does not define a sub-layer to control the connection between two bidirectionally communicating entities in the cloud, which leads to inter-entity Communication is not reliable. Therefore, this article adds a sub-layer CaaS (CommunicaTIon as a Service) layer to the IaaS layer to ensure the security of communication between the two entities. This sub-layer model is based on MPLS technology. By applying MPLS technology to the CaaS layer, the security and reliability of data transmission in the "cloud" can be improved, and DDoS and other attacks can be effectively prevented. The structure of the CaaS layer embedded in the IaaS layer is shown in FIG. 1.
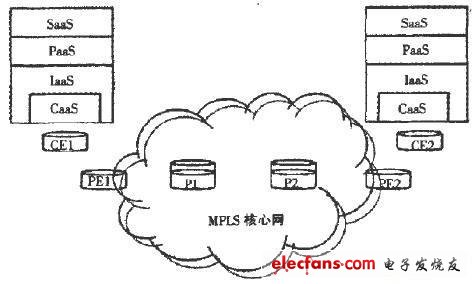
Figure 1 Structure of CaaS layer embedded in IaaS layer
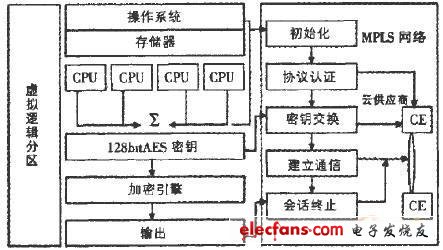
The CaaS sublayer mainly includes the following functions:
Initialization: Initialization consists of two processes. First, the CPU in the virtual logical partition is initialized to obtain a 32-bit random number, and then this will form a l28-bit session key through AES (Advanced EncrypTIon Standard, advanced encryption standard J. One key will only correspond to one logical partition. Then After the network is initialized, the communication between CE (Customer Edge, user edge device) starts.
Protocol authentication: The routing in the MPLS network verifies the data packets transmitted between each other. Attacks in MPLS networks generally occur when labeling data packets, so they can only be labeled after they have been authenticated. Routers use authentication protocols to identify routes and paths. This establishes a reliable identification mechanism between unknown networks. Data packets transmitted from unknown networks will be discarded once they fail verification, which greatly reduces the risk of attacks.
Key exchange: IKE (Internet Key, key exchange) establishes an association SA (SecurityAssociaTIon, security association) between two cloud users who need to communicate or between cloud users and cloud providers, and is responsible for key generation and management . SA can encode the protocol between the two communication subjects to confirm which algorithm, key and key length they use. IKE establishes SA in two stages: the first stage establishes a communication channel between two communication subjects and authenticates the channel, and the second stage establishes SA through the established communication channel. SA has a life cycle. When the session key expires, it will send a first-stage SA delete command to the host of the other party, and then the two parties will conduct SA negotiation again. The periodicity of the key determines that if a certain time limit is exceeded, a new key will be generated, which greatly enhances the robustness and reliability of the key. This is also an important reason for using key exchange in cloud computing.
Establish communication: The connection between CEs is established through label edge routing. In an MPLS network, LSP (Labelb Switch Path) is determined by the label between two endpoints, and is divided into two types: dynamic LSP and static LSP. Dynamic LSP is generated by routing information, while static LSP is specified. The logical partition uses the AES algorithm to encrypt data. This encryption is based on the ECB (Electronic Code Book) mode. Through this mode, the data stream is quickly transmitted to cloud users. The encryption uses a one-time key, even if the data packet is detected, it is difficult to decrypt it, so that the security of the data is fully guaranteed.
Session termination: When the cloud user ends the communication, the session will automatically terminate, and the cloud provider will charge based on the services used by the cloud user during the session. At the same time, the communication resources in the MPLS network and the cached data in the virtual processor will be released. (figure 2)
4 Summary and outlook
Security is the primary issue to consider if an enterprise chooses to move to cloud computing. We prevent these potential security risks by adding a CaaS sublayer in the IaaS layer, including the prevention of DDoS attacks. The CaaS layer is also billed according to service usage. It is used to guarantee the service quality of cloud computing and the reliability of data transmission. At present, cloud security is still in the development stage. I believe that with the continuous development of the cloud security system and the technological innovation of major security vendors, cloud security will further develop to meet the security needs of users.
Bluetooth Headphone
Bluetooth headpone also call bluetooth earphone or bluetooth earbuds,which is a headset that provides a two-way connection to the user's cellphone via Bluetooth. Fitting in one ear only, the part that is pressed slightly into the ear canal typically comes with removable small, medium and large tips.



Best Wireless Headphones,Bluetooth Head Phones,Noise Ear Buds,Best Earbuds for Running
Pogo Technology International Ltd , https://www.pogomedical.com